NOw you can easily unsend a sent email from your gmail account by following the simple steps given below :
- first of all open your gmail account
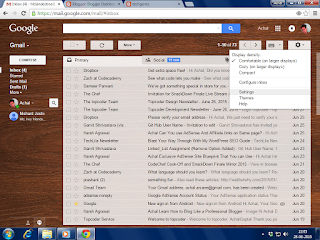
- Now go to the settings at right top corner of the screen
- under the setting option again click to the setting option
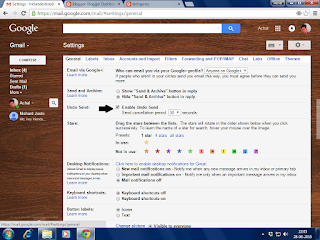
- now the setting window will appear ,under this enable the undo send option
- The best part is that you can also set the time limit to unsend an email,but the maximum time limit is 30 secind if you choose undo option within that time frame then you email could get unsent but if you tried to undo send it after that time limit than you will encounter failure
- To understand it fully let us perform it practically
- compose an email to any additional email account if you have,otherwise you can also try it to you r friend or family member whom you can easily access
- send the mail
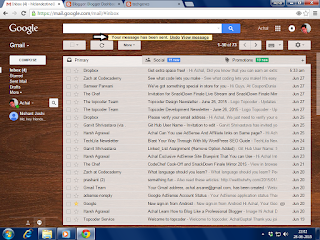
- after sending your mail a message will appear like this on your gmail window displaying the undo,view and message option in a yellow bar
- now click the undo option
- ta da you have just unsend a sent email
- You can check by logging in the account to which you have sent a mail that whether your mail was recieved or not